ISO 27001 Certification for Information Security Management System
ISO 27001:2022, is an information security standard created by the International Organization for Standardization (ISO), which provides a framework and guidelines for establishing, implementing and managing an information security management system (ISMS).
It provides a framework for organizations to establish, implement, maintain, and continually improve their information security.
ISO framework and the purpose of ISO 27001
The ISO framework is a set of international standards that provide guidelines and requirements for various aspects of business management.
ISO/IEC 27001 is a part of ISO 27000 series of standards and is specifically related to information security management.
The purpose of ISO 27001 is to provide a systematic approach to managing sensitive company information so that it remains secure.
What are the three principles of ISO 27001 information security management system?
The three main principles of ISO 27001 are:
Confidentiality:
Ensuring that information is accessible only to those authorized to have access.
Integrity:
Ensuring that information is accurate and complete and protected from unauthorized modification.
Availability:
Availability: Ensuring that authorized users have access to the information when they need it.
Why is an information security management ISO/IEC 27001 important?
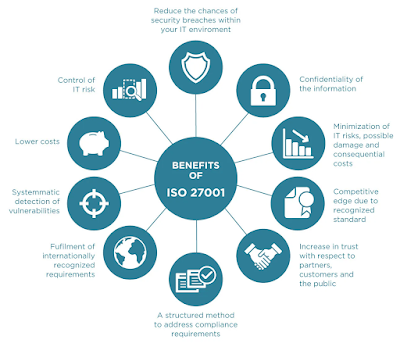
ISO 27001 will help you reduce Information security and privacy risks
ISO/IEC 27001:2022 provides a framework for organizations to implement, maintain, and continually improve their information security management system.
By following the standard's guidelines and requirements, organizations can identify and manage potential security risks, ensuring the protection of sensitive information from unauthorized access, disclosure, alteration, or destruction.
ISO 27001 means saving time and money
By implementing an ISMS based on ISO 27001, organizations can save time and money by having a systematic approach to managing their information security.
This includes identifying and managing risks, implementing and maintaining controls, and carrying out regular assessments and audits.
Respond to evolving cybersecurity and privacy threats
ISO 27001 requires organizations to continually review and improve their ISMS, which helps them stay up-to-date with the latest security threats and vulnerabilities.
This helps organizations to be more proactive in identifying and managing potential risks and ensuring the protection of their sensitive information.
Protect your data, wherever it is
ISO 27001 provides a framework for organizations to protect their sensitive information, regardless of where it is stored or processed.
This includes information stored on-premises, in the cloud, or on mobile devices. By following the standard's guidelines and requirements, organizations can ensure that their sensitive information is protected at all times.
Improve company culture
ISO 27001 helps organizations to develop a culture of information security. By following the standard's guidelines and requirements, organizations can ensure that all employees are aware of their responsibilities for protecting sensitive information.
This helps to create a culture of security, in which employees understand the importance of protecting sensitive information and are more likely to take appropriate actions to protect it.
Why Should a Company Adopt ISO 27001? Is ISO 27001 Certification Worth It?
Compliance:
Adopting ISO 27001 helps a company comply with relevant laws and regulations regarding information security, such as the General Data Protection Regulation (GDPR) and the Health Insurance Portability and Accountability Act (HIPAA). This can help companies avoid costly fines and penalties for non-compliance.
Risk Management:
ISO 27001 provides a framework for identifying, assessing and managing information security risks. By implementing ISO 27001, companies can proactively manage potential security threats and minimize their impact on the business.
Customer Trust:
ISO 27001 certification demonstrates to customers, partners, and other stakeholders that a company takes information security seriously and has implemented a robust management system to protect sensitive information. This can help build trust and improve the company's reputation.
Improved Efficiency:
ISO 27001 can help companies streamline their information security processes and identify areas for improvement. This can lead to increased efficiency and cost savings in the long run.
Continuous improvement:
ISO 27001 requires regular reviews and updates to the information security management system, ensuring that it stays current with the latest security threats and industry best practices. This encourages a culture of continuous improvement and helps companies stay ahead of emerging security risks.
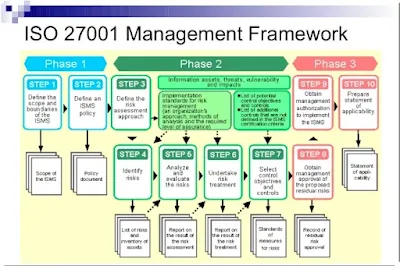
How does ISO 27001 work?
ISO 27001 provides a framework for managing information security risks and implementing controls to protect sensitive information. The process of implementing ISO 27001 typically involves the following steps:
Conduct a risk assessment:
The first step in implementing ISO 27001 is to conduct a thorough risk assessment to identify potential threats to the organization's information security. This includes identifying the assets that need to be protected, the risks to those assets, and the likelihood and potential impact of those risks.
Implement controls:
Based on the results of risk assessment, appropriate controls are selected and implemented to mitigate the identified risks. These controls may include technical measures, such as firewalls and encryption, as well as administrative measures, such as security policies and procedures.
Document the ISO/IEC:
The organization's information security management system (ISMS) should be documented, including policies, procedures, and guidelines. This documentation should be regularly reviewed and updated.
Implement a management system:
An internal management system is established to ensure that the ISMS is implemented, maintained and continually improved. This includes establishing roles and responsibilities, setting up a communication plan, and assigning resources.
Internal audit:
Internal audits are conducted to ensure that the ISMS is being implemented and maintained correctly.
Certification:
The organization can choose to have their ISMS certified by an external certification body to demonstrate their compliance with ISO 27001.
Learn more about the key features of ISO 27001
Risk Management:
ISO 27001 requires organizations to identify and manage information security risks through a systematic and ongoing process.
Control Implementation:
ISO 27001 establishes a comprehensive set of controls, including technical and administrative measures, to protect sensitive information.
Documented ISMS:
ISO 27001 requires organizations to document their ISMS, including policies, procedures, and guidelines, and to regularly review and update it.
Continual Improvement:
ISO 27001 requires organizations to continuously monitor and improve their ISMS.
Certification:
ISO 27001 has a certification option that allows organizations to demonstrate their compliance with the standard.
Holistic approach:
ISO 27001 adopts a holistic approach to information security management, taking into account the entire organization and its environment.
Legal and regulatory compliance:
ISO 27001 helps organizations to comply with relevant laws and regulations.
How Much Does the ISO 27001 Certification Cost?
The cost of ISO 27001 certification can vary depending on the size of your organization, the complexity of its systems and processes, and the accredited certification body chosen. It can range from a few thousand dollars to tens of thousands of dollars.
Why Choose us for ISO 27001?
Choosing a reputable and experienced consulting firm can help ensure that your organization is prepared for the certification process and can help you navigate requirements of ISO 27001.
Best practices for preparing for ISO 27001 certification
Best practices for preparing for ISO 27001 certification include conducting a risk assessment, implementing a management system, and establishing policies and procedures.
What are the ISO 27001 controls?
ISO 27001 controls include information security cybersecurity and privacy protection policies, procedures, and guidelines, as well as technical and operational controls.
How many controls are there in ISO 27001?
There are 114 controls in total in ISO 27001, divided into 14 control categories.
Requirements: Two parts of the standard
Part 1:
ISO 27001:2013 which sets out the requirements for an information security management
Part 2:
ISO 27001:2013 - Information technology - Security techniques - Code of practice for information security management.
How to achieve ISO 27001 compliance?
Achieving ISO 27001 compliance involves implementing the controls required by the standard, and then undergoing an independent assessment and certification process to verify that the controls are effectively implemented.
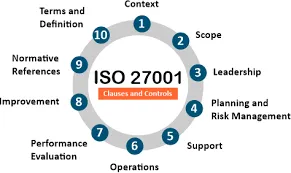
ISO 27001:2013 is divided into several clauses and subclauses, each covering a specific aspect of information security management.
Introduction
This clause provides an overview of ISO 27001, including its purpose and the benefits of implementing an ISMS.Scope
This clause defines the scope of ISMS and the applicability of the standard.Normative references
This clause lists the standards and other documents that are referred to in the standard and that are considered necessary for its application.Terms and definitions
This clause of ISO 27001 provides definitions of terms and concepts used throughout the standard. Some of the key terms and definitions included in this clause include:Information security: The preservation of confidentiality, integrity and availability of information by applying a risk management process and giving assurance that the information is protected against unauthorized access, disclosure, alteration, destruction, and disruption.
Risk: The effect of uncertainty on objectives.
Security controls: Measures, policies, procedures, or other means implemented to provide a level of protection for information and information systems.
Threat: A potential cause of an unwanted incident, which may result in harm.
Vulnerability: A weakness of an asset or control that can be exploited by one or more threats.
Information security incident: An occurrence that has or could have a negative impact on the availability, integrity, or confidentiality of an organization's information.
Business continuity: The capability of the organization to continue the delivery of products or services at acceptable predefined levels following a disruptive incident.
Compliance: Conformance with legal, regulatory, and contractual requirements.
ISO: International organization for standardization
It's worth noting that Clause 0 to 4 are considered as the general requirements for ISO 27001, but not to be considered as mandatory for certification. These clauses provide an overview of ISO 27001 and give guidance on how to understand and apply it.
Clause 4: Context of the organization,
This is the first of the four main clauses of ISO 27001:2013. It provides guidance on understanding the organization and its context, understanding the needs and expectations of interested parties, determining the scope of the ISMS, and aligning the ISMS with the organization's overall direction and business objectives.
4.1 Understanding the organization and its context
4.2 Understanding the needs and expectations of interested parties
4.3 Determining the scope of the ISMS
4.4 ISMS and the organization's overall direction and business objectives
Clause 5: Leadership
It focuses on the leadership aspect of an effective information security management system . The clause establishes the requirement for top management to take a proactive role in leading and committing to the implementation and maintenance of the ISMS.
5.1 Leadership and commitment
5.2 Policy
5.3 Organizational roles, responsibilities and authorities
Clause 6: Planning
This clause 6 pertains to the planning aspect of an effective information security management system (ISMS). It outlines the steps that organizations should take to identify and address risks and opportunities related to information security, and to develop plans and objectives to achieve a secure and compliant environment.
6.1 Actions to address risks and opportunities
6.2 Information security objectives and plans to achieve them
6.3 Information security risk assessment
6.4 Information security risk treatment
6.5 Information security controls
6.6 Planning the management of incidents
6.7 Business continuity management
6.8 Compliance with legal and regulatory requirements
Clause 7: Support
This clause pertains to the support that is required for an effective information security management system (ISMS). It outlines the need for organizations to provide the necessary resources, competence, awareness, and communication to ensure that the ISMS is implemented and maintained effectively.
7.1 Resources
7.2 Competence
7.3 Awareness
7.4 Communication
Clause 8:Operation
Operation pertains to the operational aspects of an effective information security management system (ISMS). It outlines the need for organizations to establish and maintain effective processes and controls to manage and mitigate information security risks, and to respond to and recover from security incidents.
8.1 Operational planning and control
8.2 Information security risk management
8.3 Information security incident management
8.4 Monitoring, measurement, analysis and evaluation
Clause 9: Performance Evaluation
This Clause pertains to the performance evaluation of an effective information security management system (ISMS). It outlines the need for organizations to conduct regular internal audits and management reviews to ensure that the ISMS is functioning effectively and that it meets the requirements of ISO 27001 standard.
9.1 Internal audit
9.2 Management review
Clause 10: Improvement
This clause pertains to the improvement of an effective information security management system (ISMS). It outlines the need for organizations to continuously improve the ISMS to ensure that it remains effective and relevant.
10.1 General
10.2 Nonconformity and corrective action
10.3 Continual improvement
IMPLEMENTATION & CERTICIFATION
ISO 27001 is an internationally recognized standard for information security management systems (ISMS). It provides a framework for managing sensitive company information so that it remains secure.
The standard is designed to help organizations protect information assets of the organization by implementing a comprehensive set of security controls.
ISO 27001 mandatory documents
Information Security Policy:
The Information Security Policy is a high-level document that sets out the organization's overall approach to information security. It should be approved by senior management and should be communicated to all employees.
Statement of Applicability (SoA):
The Statement of Applicability (SoA) is a document that outlines the specific controls that have been implemented to meet the requirements of ISO 27001. It should detail the controls that have been selected, the rationale for their selection, and how they have been implemented.
Risk Assessment Report:
The Risk Assessment Report is a document that outlines the risks that have been identified to the organization's information assets. It should detail the likelihood and impact of each risk, as well as the controls that have been implemented to mitigate them.
Procedures:
Procedures are detailed instructions for how specific controls should be implemented. They should be written in a clear and concise manner and should be easily accessible to all employees.
Records:
Records are an important aspect of an ISMS, as they provide evidence that the controls have been implemented and are being followed. They should be kept up-to-date and should be easily accessible to all employees.
Audit Program:
The Audit Program is a document that outlines the process for conducting internal and external audits of the ISMS. It should detail the scope, frequency, and responsibilities of the audits.
Management Review Report:
The Management Review Report is a document that summarizes the results of the management review. It should be prepared after each management review and should be reviewed by senior management.
Implementation of these documents and maintaining them with regular audits will lead to the certification of ISO 27001. An independent assessment and certification process is then conducted to ensure that the controls are effectively implemented and meet the requirements of ISO/IEC 27001 standard.
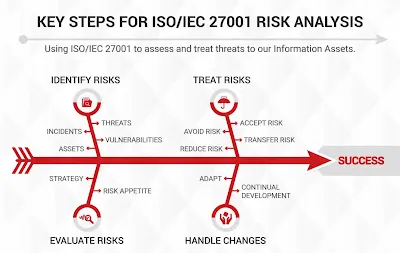
ISO 27001 and risk management
ISO 27001 is a standard for data security management that provides a framework for managing sensitive company information so that it remains secure.
The standard focuses on risk management, which is the process of identifying, assessing, and mitigating the risks to an organization's information assets.
The standard requires organizations to conduct a risk assessment to identify the risks to their information assets and to implement controls to mitigate those risks.
What is “ISO 27001 certified”?
An organization that is "ISO 27001 certified" has implemented an information security management system (ISMS) that meets requirements of the ISO 27001 standard and has been independently assessed and certified by a certification body.
This certification demonstrates that the organization has a systematic and ongoing approach to managing sensitive information and that it is taking appropriate measures to protect that information.
What is the current ISO 27001 standard?
The current version of the ISO 27001 standard is ISO/IEC 27001:2022, which was published in October 25, 2022. This version of standard replaces the previous version, ISO/IEC 27001:2013.
What is ISO 27001 information security management?
ISO 27001 information security management is a systematic and ongoing approach to managing sensitive information in order to protect it from unauthorized access, use, disclosure, disruption, modification, or destruction.
The standard provides a framework for managing information security that includes risk assessment, policies, procedures, and technical and operational controls.
What are the ISO 27000 standards?
The ISO 27000 series is a set of standards for information security management.
These standards provide a common language for data security and are designed to help organizations protect their information assets.
The series includes ISO 27001, which provides the requirements for an ISMS, and ISO 27002, which provides the code of practice for data security management.
ISO 27001 supporting standards
ISO 27001 is supported by other standards in the ISO 27000 series, such as ISO 27002, which provides a code of practice for information security management, and ISO 27005, which provides guidelines for data security risk management.
Other standards that support or complement ISO 27001 include ISO 27017, ISO 27018, ISO 22301, and NIST SP 800-53.
Frequently Asked Questions:
- What
is ISO 27001? ISO 27001 is an international standard for Information
Security Management Systems (ISMS). It provides a systematic approach to
managing sensitive company information, ensuring its confidentiality,
integrity, and availability.
- How
to do risk assessment ISO 27001? To conduct a risk assessment for ISO
27001 compliance, follow these steps: identify assets, assess threats and
vulnerabilities, calculate risks, prioritize risks, and implement
appropriate controls to mitigate identified risks.
- What
is information security? Information security refers to the practice
of protecting sensitive information from unauthorized access, use,
disclosure, disruption, modification, or destruction. It involves
safeguarding both digital and physical information assets.
- What
is social engineering in information security? Social engineering is a
technique used by malicious actors to manipulate individuals into
revealing sensitive information or performing actions that compromise
security. It often involves psychological manipulation and deception.
- How
to be an information security analyst? To become an information
security analyst, typically, one needs a degree in cybersecurity or a
related field, along with relevant certifications such as CISSP, CISM, or
CompTIA Security+. Gaining practical experience through internships or
entry-level positions is also valuable.
- What
is cryptography in information security? Cryptography involves the use
of mathematical algorithms to convert data into a secure and unreadable
format, making it unintelligible to unauthorized parties. It plays a
crucial role in ensuring data confidentiality and integrity.
- What
is an information security policy? An information security policy is a
set of guidelines and rules that an organization defines to ensure the
proper handling, protection, and usage of its information assets. It outlines
the framework for implementing security measures.
- What
is risk assessment in information security? Risk assessment in
information security involves identifying potential threats and
vulnerabilities, evaluating their impact and likelihood, and determining
appropriate risk treatment strategies to protect information assets.
- What
is the definition of information security? Information security is the
practice of protecting sensitive and valuable information from
unauthorized access, disclosure, alteration, destruction, or disruption to
ensure the confidentiality, integrity, and availability of the
information.
- How
are policy, standard, and procedure related in information security?
In the context of information security, policies set high-level
objectives, standards define specific requirements, and procedures provide
detailed step-by-step instructions on how to implement and adhere to those
standards.
- How
to implement information security management? Implementing information
security management involves developing an ISMS based on ISO 27001
principles, defining security policies, conducting risk assessments,
implementing security controls, and regularly monitoring and reviewing the
system.
- What
are the key issues related to information security? Key issues related
to information security include data breaches, insider threats, malware
attacks, weak passwords, lack of security awareness, and compliance with
relevant regulations.
- What
is auditing in terms of information system security? Auditing in
information system security involves assessing and evaluating an
organization's security controls and practices to ensure they align with
policies, standards, and regulations, and to identify areas for
improvement.
- What
is cost-benefit analysis in information security? Cost-benefit
analysis in information security is the process of evaluating the
potential costs of implementing security measures against the benefits of
reducing risks and potential losses due to security incidents.
- What
is data protection and information security? Data protection involves
safeguarding personal or sensitive information from unauthorized access or
misuse, whereas information security covers a broader spectrum of
practices to protect all types of information assets within an
organization.
- What
is layered security strategy in information systems? A layered
security strategy involves deploying multiple security measures at
different levels to protect an information system. This approach ensures
that even if one layer is breached, other layers will still provide
protection.
- What
is physical security of information technology infrastructure?
Physical security of information technology infrastructure refers to
protecting the hardware, facilities, and physical components of an
organization's IT systems from unauthorized access, theft, or damage.
- What
is social engineering in the context of information security? Social
engineering in the context of information security involves manipulating
people, often through psychological tactics, to gain unauthorized access
to systems, information, or confidential data. It is a common tactic used
in phishing attacks and other forms of cybercrime.
It is important to work with a reputable ISO consultant like ISO Certification in Nepal Pvt. Ltd. that can provide cost effective expert guidance and support to your organization throughout the process of ISO 9001 implementation. We are the leading ISO System Certification body in Nepal. We will help an organization to understand requirements, implement the standard and ensure that your company is in compliance with any ISO Certification in Nepal. Besides to ISO 9001 quality management system, we also provide ISO 14001( Environmental management System certification) , ISO 22000(Food Safety Management System Certification) ISO 45001 Occupational health and safety management system , ISO 27001 Information Security Management System . ISO/IEC 17025 Testing and calibration laboratories Organic Certification in Nepal. If you have any queries as well as if you want to get your organization to be ISO Certified, please call 9840525565 to get free consultation on ISO Certification service and know which ISO standards is best for your organization.